The plugin writes failed logins to a custom SQL table and optionally blocks recurring break-in attempts, the data can be used for attack statistics or to create a firewall blocklist.
By reducing the number of allowed login failures from a single host, the attack surface of a plain WordPress site is drastically lowered.
Limiting access to authenticated functions of xmlrpc prevents exploitation of a native (un)security feature that allows an attacker to try hundreds och username and password in a single request.
Se this article for more info on XMLRPC
https://blog.sucuri.net/2015/10/brute-force-amplification-attacks-against-wordpress-xmlrpc.html
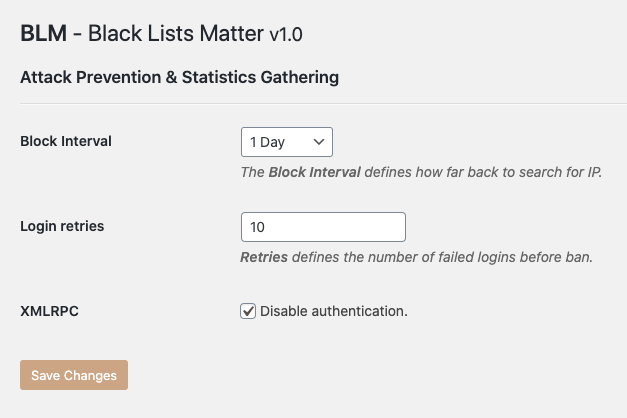
Configuration
- Block intervals
How far back in history to check for an IP, the values are predefined as: Disabled, 1 Hour, 12 Hours, 1 Day & 30 days. - Login retries
number of allowed login failures within “block interval” before banning host. - XMLRPC
Disable features that allow authentication.
The plugin also provides a set of shortcodes for displaying statistics on the frontend.
Shortcode query options
The query type “list” fetches a chronologic group of entries from the database in ascending or descending order, while “top” fetches the list by highest count. The “limit” restrict the number of entries returned.
- query = list | top
- field = id | time | ip | name | password
- limit = (int)
- sort = ASC | DESC
Top Failed Passwords
brute_table query="top" field="password" limit=10 sort="DESC"
| PASSWORD | COUNT |
|---|---|
| asbra | 792 |
| admin | 743 |
| 123456 | 583 |
| xn--1ca | 448 |
| password | 422 |
| admin123 | 386 |
| pass | 366 |
| admin@123 | 323 |
| 12345 | 314 |
| 123456789 | 309 |
Top Attacking IP
brute_table query="top" field="ip" limit=10 sort="DESC"
| IP | COUNT |
|---|---|
| 188.240.208.26 | 6270 |
| 40.76.40.117 | 3225 |
| 13.78.168.134 | 999 |
| 193.142.146.202 | 383 |
| 20.50.114.95 | 265 |
| 89.35.39.180 | 150 |
| 85.204.246.240 | 126 |
| 193.142.146.4 | 99 |
| 188.213.49.210 | 91 |
| 5.188.62.147 | 87 |
Failed Passwords, 24h
brute_table query="top" field="password" limit=10 sort="DESC" interval="1 DAY"
Attacking IP, 24h
brute_table query="top" field="ip" limit=10 sort="DESC" interval="1 DAY"
Latest Attacks
brute_table limit=10 field="time,ip,name,password" sort="DESC"
| TIME | IP | NAME | PASSWORD |
|---|---|---|---|
| 2021-04-13 07:36:24 | 13.53.64.97 | asbra | shaggy |
| 2021-04-13 07:36:24 | 13.53.64.97 | asbra | taurus |
| 2021-04-13 07:36:23 | 13.53.64.97 | asbra | brother |
| 2021-04-13 07:36:23 | 13.53.64.97 | asbra | fyfcnfcbz |
| 2021-04-13 07:36:23 | 13.53.64.97 | asbra | holiday |
| 2021-04-03 01:02:31 | 185.236.42.214 | asbra | 132 |
| 2021-03-09 15:20:09 | 185.236.42.91 | asbra | 343212 |
| 2021-03-07 14:21:25 | 185.236.42.91 | asbra | myhome |
| 2021-03-03 18:33:22 | 185.236.42.27 | asbra | 10000 |
| 2021-03-03 00:23:05 | 5.153.234.68 | asbra | adm1 |
